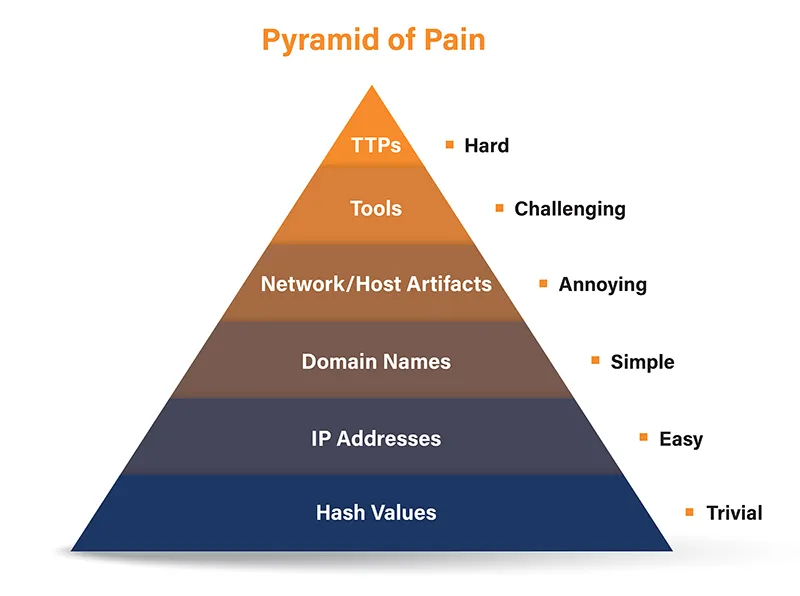
A pyramid of pain is a conceptual Cybersecurity model that categorizes IOC Indicator of Compromise and TTC Tactics, Techniques & Procedures, based on how difficult tit would be for attacker to change.
This conceptual model is applied to Cyber Security solutions like Sentinel One, CISCO Security & SOC RADAR to improve the effectiveness of CTI , Threat Hunting & Incident Response Exercise.
This Pyramid consist of 6 Levels ranging from Trival to Tough for attacker:
- Hash Values.
- IP Addresses
- Domain Name
- Host Artifacts
- Network Artifacts
- Tools
- TTP’s
Hash Values
A Hash is a numeric value of fixed length that uniquely identifies data. Hash is a result of a hashing algorithms. Some common hashing algorithms are MD5 (128 bit) , SHA-1 (160 bit), SHA-2 (256 bit)
Keep in mind that a Hash is a unidirectional function, which means it cannot me reversed, wherein, Encryption can be reversed and get the file into its original state by using respective decrypting key.
HASH is also not cryptographically secure if two files has the same has value.
Security professionals usually use the hash values to gain insight into a specific malware sample, a malicious or a suspicious file, and as a way to uniquely identify and reference the malicious artifact.
Tools that can be used to check hash values are VirusTotal & MetaDefender Cloud- OPSWAT
Above tools store the has values and sends the has value across the Antivirus so its easy to spot a malicious file if we have the hash in our arsenal. However, as an attacker, modifying a file by even a single bit is trivial, which would produce a different hash value. With so many variations and instances of known malware or ransomware, threat hunting using file hashes as the IOC (Indicators of Compromise) can become difficult.
IP Addresses
As the name suggests, An IP address is used to determine the location of a node within the network, almost ever device that has networking capabilities has an IP address, we will not dive into fundamentals of IP addresses, instead we will see how an IP could be an Indicator.
A Common defene tactic against a suspicious IP is to drop, block and deny any inbound traffic from the IP on your parameters, but this could be an easy comeback for an attacker as IP address can be changed.
Moreover, Attacker can use a Fast Flux is order to make it challenging to block the IP.
Fast Flux is a DNS technique that allows hiding phishing, malware delivery, malware communication behind a compromised host system acting as a proxy. The purpose of using the Fast Flux network is to make the communication between malware and its command and control server (C&C) challenging to be discovered by security professionals.
So, the primary concept of a Fast Flux network is having multiple IP addresses associated with a domain name, which is constantly changing
Domain Name
Domain Names can be a little more of a pain for the attacker to change as they would most likely need to purchase the domain, register it and modify DNS records. Unfortunately for defenders, many DNS providers have loose standards and provide APIs to make it even easier for the attacker to change the domain.

Can you spot anything malicious in the above screenshot? Now, compare it to the legitimate website view below:

This is one of the examples of a Punycode attack used by the attackers to redirect users to a malicious domain that seems legitimate at first glance.
What is Punycode? As per Wandera, “Punycode is a way of converting words that cannot be written in ASCII, into a Unicode ASCII encoding.”
What you saw in the URL above is adıdas.de which has the Punycode of http://xn--addas-o4a.de/
Internet Explorer, Google Chrome, Microsoft Edge, and Apple Safari are now pretty good at translating the obfuscated characters into the full Punycode domain name.
To detect the malicious domains, proxy logs or web server logs can be used.
Attackers usually hide the malicious domains under URL Shorteners. A URL Shortener is a tool that creates a short and unique URL that will redirect to the specific website specified during the initial step of setting up the URL Shortener link. According to Cofense, attackers use the following URL Shortening services to generate malicious links:
- bit.ly
- goo.gl
- ow.ly
- s.id
- smarturl.it
- tiny.pl
- tinyurl.com
- x.co
You can see the actual website the shortened link is redirecting you to by appending “+” to it (see the examples below). Type the shortened URL in the address bar of the web browser and add the above characters to see the redirect URL.
HOST Artifacts
Host artifacts are the traces or observables that attackers leave on the system, such as registry values, suspicious process execution, attack patterns or IOCs (Indicators of Compromise), files dropped by malicious applications, or anything exclusive to the current threat.
Network Artifacts
Adversaries’ network activities that are observable. Typical examples include URI patterns, C2 information embedded in network protocols, distinctive HTTP User-Agent, or SMTP Mailer values, etc.
Tools
Software used by attackers to accomplish their mission. This includes utilities designed to create malicious documents for spear phishing, backdoors used to establish C2 or password crackers, or other host-based utilities
Antivirus signatures, detection rules, and YARA rules can be great weapons for you to use against attackers at this stage.
MalwareBazaar and Malshare are good resources to provide you with access to the samples, malicious feeds, and YARA results – these all can be very helpful when it comes to threat hunting and incident response.
For detection rules, SOC Prime Threat Detection Marketplace is a great platform, where security professionals share their detection rules for different kinds of threats including the latest CVE’s that are being exploited in the wild by adversaries.
Fuzzy hashing is also a strong weapon against the attacker’s tools. Fuzzy hashing helps you to perform similarity analysis – match two files with minor differences based on the fuzzy hash values
TTC’s
TTPs stands for Tactics, Techniques & Procedures. This includes the whole MITRE ATT&CK Matrix, which means all the steps taken by an adversary to achieve his goal, starting from phishing attempts to persistence and data exfiltration.
If you can detect and respond to the TTPs quickly, you leave the adversaries almost no chance to fight back. For, example if you could detect a Pass-the-Hash attack using Windows Event Log Monitoring and remediate it, you would be able to find the compromised host very quickly and stop the lateral movement inside your network. At this point, the attacker would have two options:
- Go back, do more research and training, reconfigure their custom tools
- Give up and find another target
Well at this stage attacker would leave the premises and try to get back once they have forged enough tools to set your network back again, Pyramid of Pain is a good defence concept if implemented properly, and it can get adversaries annoyed. Hope you liked the blog.
Happy Hacking!!!
