Hey Hackers !!!
Hope you’re doing well and enjoying the long weekend, Welcome to the next episode in our Cybersecurity Foundation series, today we are going to discuss and understand what’s risk and some steps in order to manage those risks, as always we gonna gel our learning with some real life examples for better comprehension of the topic, So lets dive into the discussion without any further dues.
Threat & Risks
Risk is defined as the probability that an event will occur, in a typical business environment risk is referred as an event or action that can negatively impact their computational environment, wherein Threat is a specific type of risk, that is defined as an action or occurrence that could lead to breach in a security, outage or corruption of system’s due to the exploitation of any known or unknown Vulnerability.
In order to tackle with such Threat’s & Risk’s companies develop various Threat & Risk Management Plans, which is the process of Identifying, Assessing & Prioritizing the risks. A Risk Management plan help organizations to eliminate the risk completely or minimize the impact of risk to certain extent is elimination is not possible.
Risk Management Plan
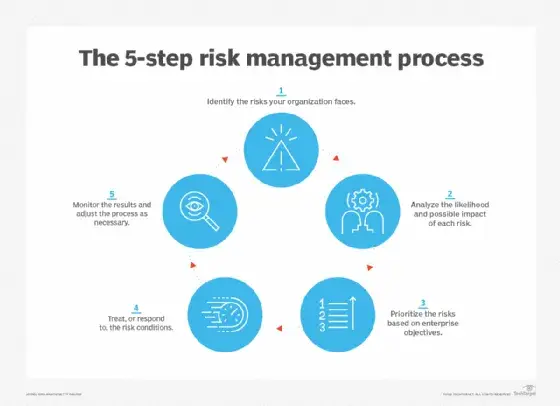
Let’s discuss what are the steps involved in a Risk Management Plan, The very first step in a Risk Management plan is Risk Assessment, It is a process of identifying the risks that might impact the environment.
In A sophisticated risk assessment environment, It is common to record risks in a Risk Register, which is a formal documentation that list’s risk, their impact, controls & other information required by Risk Management Plan.
Once, The identification of the risks is done the next step is Evaluating the Risk for two major factors, First, The likelihood that the risk will occur in the environment, for example, Floods occurs frequently or the likelihood of its occurrence is much higher in Louisiana then in Mount St. Helens, Washington. the aforesaid example is used to represent the complete loss of facility. After you determine the likelihood of risk the second factor you need to look after is The Impact of the risk on to your environment. A Ransomware attack on a single user might not impact to the business, though it will adversely affect the user, A ransomware attack on to a server will have much higher impact then a single user.
Once you’re done with Risk Evaluation the next step is Risk Prioritization, One mechanism that can help you to prioritize the risk is by creating a Risk Matrix, It takes several factors into consideration in order to rank the risk, these factors are :
- The Risk.
- The Likelihood of the risk that it will occur.
- The Impact of Risk.
- Total Risk Score.
- A relevant Business owner of risk.
- what Core Principles of security the Risks affects ( Confidentiality, Integrity & Availability)
- What are the strategies and steps required to eliminate or minimize the risk.
One of the best way to get the Total Risk score is to number both the Likelihood & Impact of risks between 1 to 10 and then multiply both the scores and then rank the final score in descending order, wherein the highest score represents High Risk & Impact and vice-versa, Initially you can rank total risk score this way but when other factor such as cost, available resources and other factors get involved in this this prioritization can change.
After conducting all the steps mentions above Risk Assessment, Evaluation & Prioritization, you will be left with 4 general risk response strategies, Let’s discuss all.
- Risk Avoidance.
- Risk Acceptance.
- Risk Mitigation.
- Risk Transfer.
Risk Avoidance, is the step taken to eliminate the risk by choosing not the engage in any action or activity related to risk, There’s a frequent problem with the risk is that it always comes with reward, by avoiding the risk you often loss the reward associated with it, A typical example of this can be seen in casino, there is a possibility that you win a million dollar, but you could also lose, but if you’r not choosing to indulge into a game of Roulette, you’re losing the reward straight away.
Risk Acceptance, is the process of gathering all the information related to the risk and then making an informed decision of accepting the impact and likelihood risk. In above casino example, Risk aceptance would be a process wherein a player would first try to understand the game by understanding the variants, concept of house edge, Knowing the odds and many more, and then taking the decision the accept the risk associated with it and continue playing along with the risk.
Risk Mitigation, as the a name suggests it is the process of eliminating the risk completely or the minimize the risk so that least belongings a impacted, one such example of this could be the concept of backups It is impossible to reverse a ransomware attack, cause they mostly uses one way encryption, this is a type of risk that cannot be mitigated so we minimize the loss of data by conducting regular backups.
Risk Transfer, This is the steps taken to deal with risk by moving the responsibility of risk to third party organization via Insurance. Purchasing the insurance assure that even if the event occurs the loss is then taken care by insurance companies and not by the organization.
However this is not the Only risk Management plan that organization follows, Many companies follows different approach in order to tackle with risks based on their current requirements and Organizations Security Maturity Levels.
Well, That’s everything about Risk Management Plan, hope you liked this Episode, Make sure to dig deeper into this topic cause a solid base builds a skyscraper.
Happy Hacking!!!!

