A distributed denial-of-service (DDoS) attack targeting a financial institution in the United Arab Emirates has set new records for both duration and sustained volume of requests. The attack, attributed to the pro-Palestinian hacktivist group BlackMeta (also known as DarkMeta), lasted six days and involved multiple waves of web requests lasting between four to 20 hours, according to cybersecurity firm Radware.
Attack Overview
The DDoS attack, which lasted more than 100 hours in total, averaged 4.5 million requests per second. This represents a significant departure from typical hacktivist denial-of-service attacks, which usually last between 60 seconds to five minutes. Pascal Geenens, director of threat intelligence for Radware, noted the unprecedented scale and persistence of this attack, stating, “Now, in the case of this attack, the campaign in total lasted six days, and in those six days, 70% of the time, that customer was being targeted by an average of 4.5 million requests.”
BlackMeta’s History and Motivations
BlackMeta, which appeared in November 2023, has a history of claiming responsibility for attacks against organizations in Israel, the UAE, and the US. The group has previously targeted the San Francisco-based Internet Archive and Israel-based infrastructure of the Orange Group. BlackMeta is motivated by a pro-Palestinian ideology and has an anti-Western stance, with apparent links to Russia, using Arabic, English, and Russian in its communications.
Attack Details
The DDoS attack on the UAE financial institution was announced by BlackMeta on Telegram days before the operation. The cyberattack overwhelmed the financial firm’s website with requests, reducing legitimate traffic to as low as 0.002%, with an average of 0.12%. The attackers utilized a cybercrime service known as InfraShutdown, which costs between $500 to $625 a week.
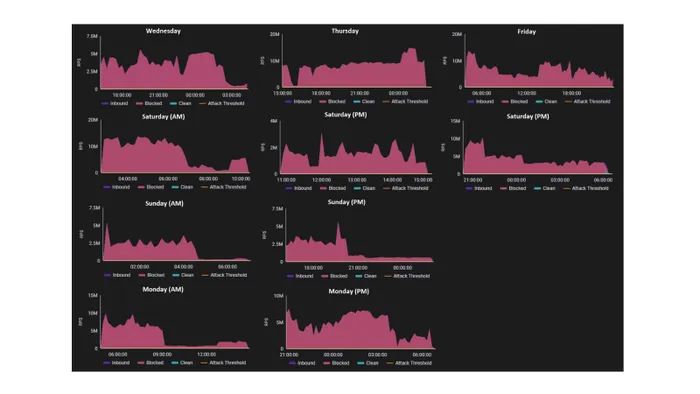
Monetization and Tactics
Radware’s advisory suggests that BlackMeta is likely a rebrand of Anonymous Sudan, a group known for its attacks alongside the pro-Russian Killnet group. Anonymous Sudan advertised the InfraShutdown DDoS service, indicating financial benefits from its hacktivism. The group’s attacks are framed as retribution for perceived injustices against Palestinians and Muslims, targeting critical infrastructure such as banking systems, telecommunication services, government websites, and major tech companies.
Challenges in Mitigation
Rate-limiting bandwidth is not an effective solution against sustained application-layer attacks like this one. Pascal Geenens explained, “With the attacks going to Layer 7 — the application layer — the problem has shifted. Before we were at the network level, you could use a firewall, but that is too much processing power, so we moved to network protection. But when you move one layer up [to Layer 7], they can target specific pages and randomize the queries that they put in, so they make it look like legitimate posts.”
Conclusion
The record-breaking DDoS attack on a financial institution in the UAE by BlackMeta highlights the evolving threat landscape and the challenges in defending against sophisticated, prolonged cyberattacks. Organizations must continually adapt their security strategies to address these emerging threats and ensure robust protection of their critical infrastructure.


Aug 31, 2024 -
Your article helped me a lot, is there any more related content? Thanks!
Oct 1, 2024 -
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Nov 3, 2024 -
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.