Hey Hackers!!!
Hope you’re doing well, I am starting a new series of blogs wherein i polish my Foundations of Security, ranging from basics core principles of cybersecurity to advanced topics as we move further. I am also going to discuss about Security Policies their development, how to apply stringent controls in your environment and many more.
Today I will be Discussing on Some Basic Security Principles, to have a strong foundation for later complex and granular topics.
Core Security Principles
Building a strong fundamental knowledge of security is very important before you even start securing your business environment, You can buy firewalls, SIEM, and other fancy tools, but unless you know what needs to be protected and why does it needs to protected you’re business is just burning economy.
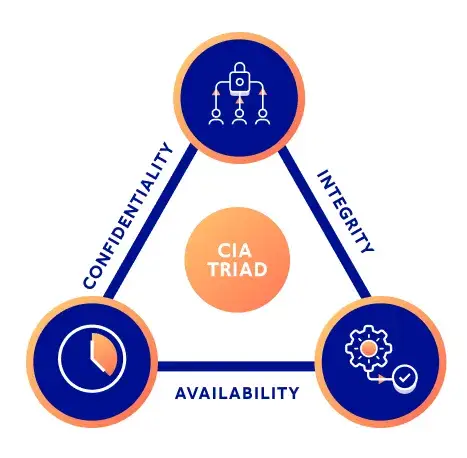
When you start learning about Security the very first acronym you come across is CIA, Which stands for :
- Confidentiality.
- Integrity.
- Availability.
Lets discuss each of CIA Triads, Starting with Confidentiality.
Confidentiality
Confidentiality is a term that deals with keeping information, Networks and systems secure from unauthorized access. In other words, Information should only be accessible to permitted users.
Let’s take an example to better understand the concept, your Banks account details, should only be accessed by you and the bank, no other user is allowed to access your information, we expect our Bank to keep our information confidential. These information holds a value and leakage of such info can lead to various breaches such as perpetrate identity theft against user.
In order to apply confidentiality organization can apply multiple technologies such as Strong Encryption, Strong Authentication & Stringent Access Controls.
Before you apply these technology to achieve confidentiality, it is very important to classify which data should be labeled as confidential, Organization uses categorizing methods to classify the data whether its Public, Internal Use Only, Confidential or Highly Confidential. One can use classification method to find which information needs to be protected. Classifying information and assets plays a important role in order to achieve confidentially.
Integrity
Integrity in Information Security refers to Consistency, Accuracy & Validity of data or information. The primary goal is to assure that the information is protected from any unauthorized or accidental changes. Organization can imply procedures and policies to assure that the information is not altered by any unauthorized user.
These policies and procedures used to effectively ensure the integrity of information includes authorization, authentication & accounting. Rights & permission can be applied on users to ensure information is accessed by authorized users, a hashing function can be used to determine any change in the information, finally any changes made should be recorded by the the system.
Availability
Availability is the terms that assure the information is available to authorized users, computers, application whenever required. There are Two types of threats associated with Availability – Accidental & Deliberate.
Accidentals Threat to Availability includes natural calamities like earthquake, floods and any other natural phenomenon that refrain’s a user to access the information.
Wherein Deliberate Threat that results into outage is realted to exploitation of any known or unknown vulnerability such as a Denial-Of-Service Attack, an Ransomware attack and many more.
In case of any such even one needs to figure out which category the outage fits in, Companies handle both Accidental and Deliberate outages differently.
These are the core principles of security, this discussion was short but one should walk before running, you can also listen to this Series of Cybersecurity Fundamental on my Spotify channel
